🚀【StegoGuard】User Guide
From the Developer
【StegoGuard】is a professional internet tool that focuses on text encryption and steganography scenarios. Its technical core deeply integrates underlying computer technologies—including cryptographic algorithms, multi-dimensional string encoding/decoding, and binary escape processing—to build a comprehensive security protection framework.
With "security, privacy, and reliability" as its core design goals, the tool not only ensures the security of data processing through technical means but also makes a clear commitment to protecting user rights: it does not store any user data throughout the entire process and supports offline use without an internet connection. This guarantees full-link privacy control of user information, from processing to storage, providing professional-grade tool support for users with high data security requirements.
Step-by-Step Operations
Ciphertext Hiding Process
-
Execute Encryption
Visit and navigate to the app’s homepage: https://www.stegoguard.top. Click to select "Ciphertext Hiding". Enter the decoy message (the "cover" message you want to send) in the Plaintext Area, and input the actual content you wish to convey in the Ciphertext Area. Finally, click the "Execute Encryption" button. -
Encryption Password (Optional)
You can pre-agree on a set of passwords with your contacts. Entering these passwords before clicking "Execute Encryption" will make your shared secrets even more secure. -
Send the Message
After clicking "Execute Encryption", the processed text message will appear in the Processing Result Area below. Select all the text, copy it, and paste it into social platforms like QQ or WeChat to send it. -
Operation Diagram
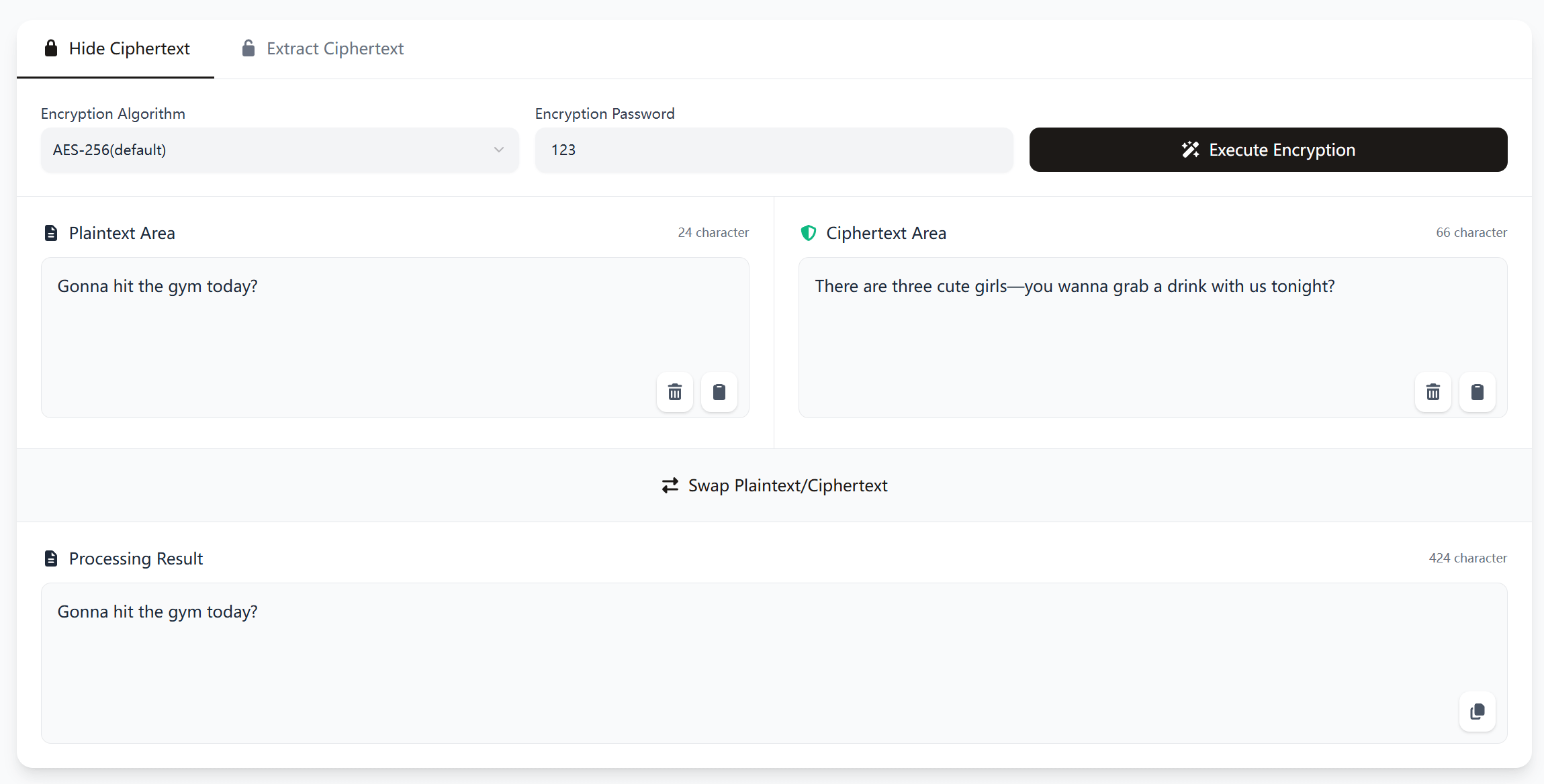 Figure 1: Execute Encryption Diagram
Figure 1: Execute Encryption Diagram
Ciphertext Extraction Process
-
Execute Decryption
Visit and navigate to the app’s homepage: https://www.stegoguard.top. Click to select "Ciphertext Extraction". Paste the text message sent by your contact into the Text String Area. If you and your contact pre-agreed on a password, enter it in the Decryption Password Area. -
Operation Diagram
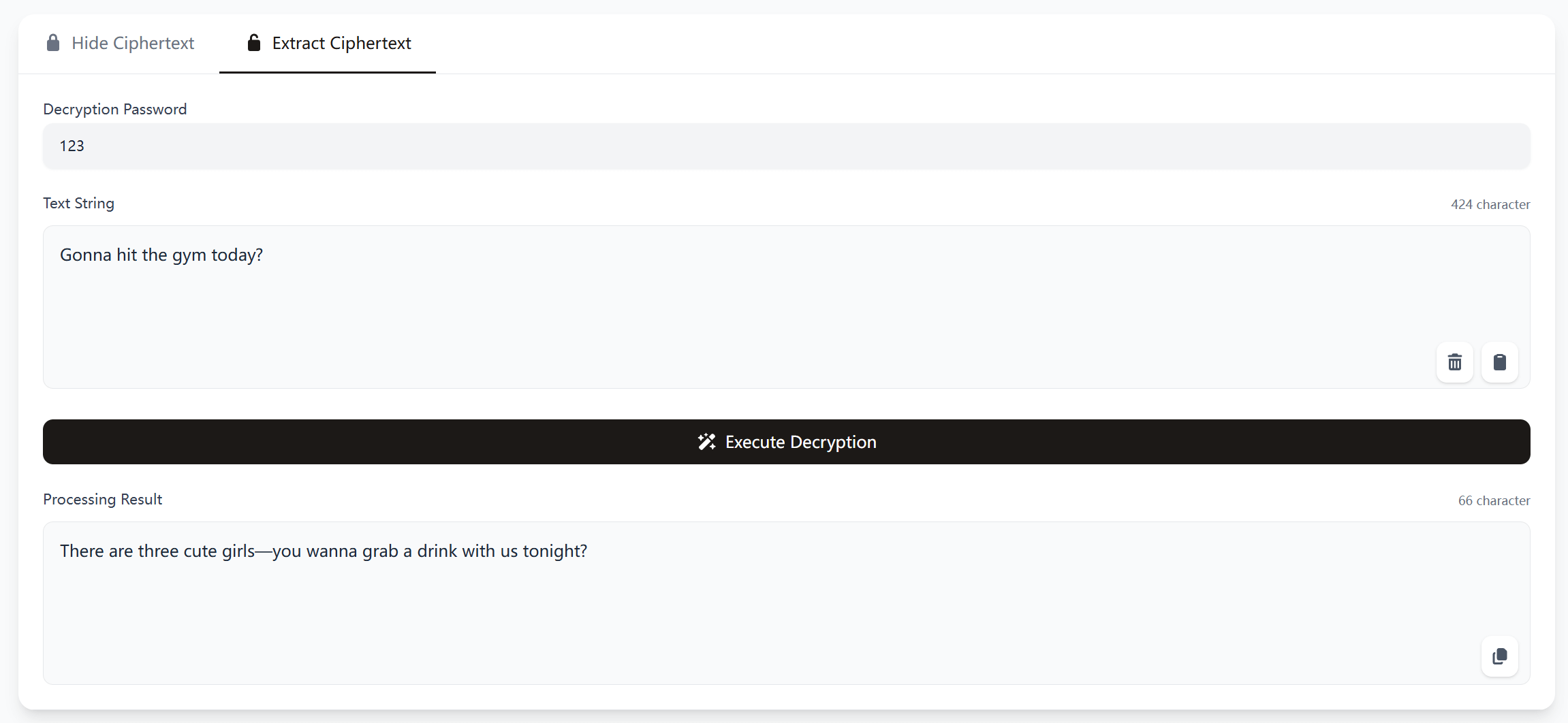 Figure 2: Ciphertext Extraction Diagram
Figure 2: Ciphertext Extraction Diagram